Hello guyz,
This time lets go through a very simple method how you as a administrator can audit domain Log On so that you can track down / audit domain users that successfully & failure log on to their profile.
When we are talking about audit, of course it also related to security issue.
All IT Administrator understand that protecting IT infrastructure has always been a priority for organizations. Many security risks threaten companies and their critical data. When companies do not have adequate security policies, they can lose data, experience server unavailability, and lose credibility.
To help protect against security threats, companies must have well-designed security policies that include many organizational and IT-related components. Organizations must evaluate security policies on a regular basis, because as security threats evolve, so too must IT evolve.
Well, enough said.. lets start the step by step…
1 – Open your Group Policy Management and create a new GPO (for this demo, i created a new GPO called Domain Log on Auditing and link to the domain root.)
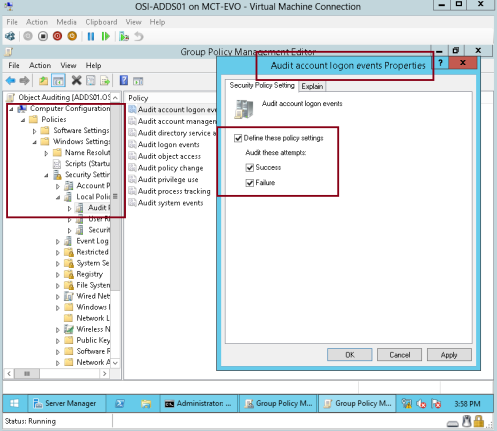
2 – Next, edit the new GPO you created just now and browse to Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies and click Audit Policy, then double click Audit account logon events..
— In the Audit account logon events Properties, click Define these policy settings box, and then select both the Success and Failure boxes and click OK.
3 – Next, Log in to your client PC, and to give a try if this function ever works, try log in with any domain users and simply key in wrong password…
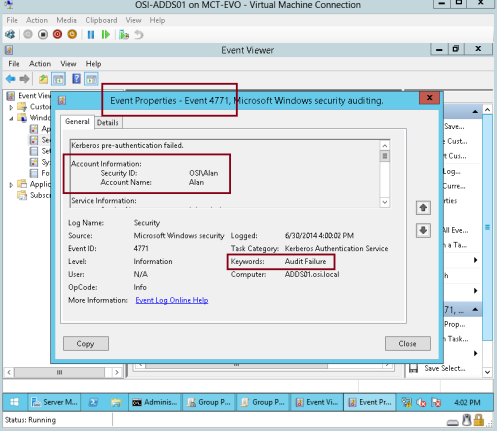
4 – Next, return to your domain server, and open Event Viewer and browse toSecurity and search for Event ID 4771, you will notice that keyword : Audit Failure, on the Account Information :, you will notice the domain user name listed.
5 – If your domain users successfully log in to their profile, and also can track down the audit event with the Event ID no 4624..



No comments:
Post a Comment